Recently I completed 11 years of my professional career. I started my career as a Customer Support Engineer then a Network Engineer and then gradually I upgraded myself to a Pre Sales Consultant. During all these years I designed and configured hundreds of networks. With the help of this article I wish to share name of 10 technologies which are part of almost all networks. Your network would hardly be functional without most of these technologies. Without wasting any more bytes let’s get straight to work.
First in the list of these technologies is –
Auto Negotiation –


Have you ever wondered why Ethernet link works most of the times, without any configuration changes? Power behind this flexibility is Auto-negotiation. Auto-negotiation is an Ethernet procedure by which two connected devices choose common transmission parameters, such as speed, duplex mode, and flow control. In this process, the connected devices first share their capabilities regarding these parameters and then choose the highest performance transmission mode they both support. In the OSI model, auto-negotiation resides in the physical layer. The protocol that became IEEE 802.3 clause 28 was developed from a patented technology by National Semiconductor known as NWay.
Virtual LANs –
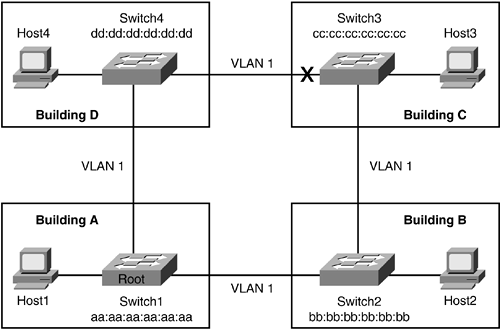

Just try to imagine the possible ways to contain broadcast in a network or apply security policies among departments or just doing a business related segregation of your network users. The only possible way to accomplish these and many more similar tasks which comes to our minds is VLAN (Virtual LANs). A VLAN is a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire, when in fact they are located on a number of different LAN segments. Because VLANs are based on logical instead of physical connections, they are extremely flexible.
VLANs define broadcast domains in a Layer 2 network. A broadcast domain is the set of all devices that will receive broadcast frames originating from any device within the set. Broadcast domains are typically bounded by routers because routers do not forward broadcast frames. Layer 2 switches create broadcast domains based on the configuration of the switch. VLANs are often associated with IP subnetworks. For example, all of the end stations in a particular IP subnet belong to the same VLAN. Traffic between VLANs must be routed. You must assign LAN interface VLAN membership on an interface-by-interface basis (this is known as interface-based or static VLAN membership).
VLAN Trunking Protocol (VTP)


VLAN is a fantastic technology, which allows us to scale Ethernet networks to any level today but creating same VLANs on hundreds of switches can bore anybody to death. There comes this awesome innovation to rescue us – VLAN Trunking Protocol (VTP). It’s a Cisco proprietary protocol that propagates the definition of Virtual Local Area Networks (VLAN) on the whole local area network. To do this, VTP carries VLAN information to all the switches in a VTP domain. VTP advertisements can be sent over ISL, 802.1Q, IEEE 802.10 and LANE trunks.
With VTP you just have to create a VTP server and create all VLANs on it and then all you have to do is just add client switches into network with few commands for VTP configuration and the magical wand will do the rest. Can’t resist myself to show this image from Wikipedia. One of the best and simplest explanation of VTP –
The comparable IEEE standard in use by other manufacturers can be implemented with GVRP or the more recent MVRP.
Link Aggregation (LAG, EtherChannels)


Uplinking 48 Gigabit ports on single gigabit links never made sense to me. In a properly designed client server architecture, 48:1 Access – Uplink bandwidth is too undersized. Thanks to Link Aggregation which allows multiple physical Fast Ethernet links to combine into one logical channel. This allows load sharing of traffic among the links in the channel as well as redundancy in the event that one or more links in the channel fail. EtherChannel can be used to interconnect LAN switches, routers, servers, and clients via UTP cable or single-mode and multimode fiber.
Default Routing
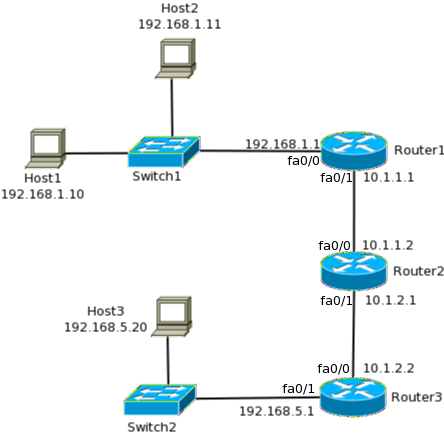

This one feature of utter simplicity, which hooks up thousands of user to the internet every day. Default routing is used to specify the gateway of last resort for your IP packets. After you had mentioned next hop for all known destinations, you use this super power to route your traffic to all unknown destinations. I am sure everybody loves this feature as much I do and knows how and where to use it very well. It won’t require further discussion.
Static Routing




Guess what is the most widely used network traffic routing system? It’s not RIP, EIGRP, OSPF or ISIS, Yeah It’s static routing. This is probably the simplest way (but static) to tell our routers, where to head for which destinations. I personally recommend doing a solid hands on with static routing while preparing for your certifications. It helps you understand the actual hop by hop traffic flow into the network and also gives you an insight why a protocol might or might not choose any particular path to any destination. When using smart media like serial, E1 or T1 you can also use floating static routes to enjoy automatic failover.
Access Control List (ACL)
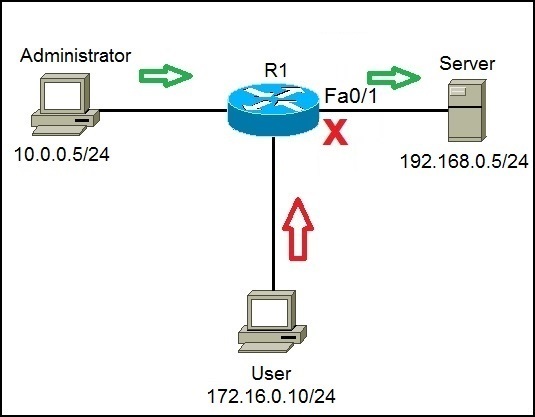

Whether you wish to perform traffic filtering, implement quality of service or do some policy based routing. One technology you just cannot do without is Access Control Lists (ACL). Also my favorite NAT too needs ACL. ACL is very simple and easy to use mechanism to identify and filter traffic on the basis of source or/and destination IP, TCP/UDP port numbers or sometimes even MAC address. No matter what stream of technology you wish to pursue in networking, it could be VoIP, Security, Routing & Switching or Wireless, you just can’t survive without good knowledge of access lists.
Network Address Translation (NAT)


One of my personal favorites. This technology has been an internet savior for so many years. It allowed internet users to overcome the scarcity of IPv4 addresses for all these years when researchers were creating mighty IPv6. NAT allows private IP networks that use unregistered IP addresses to connect to the Internet. NAT operates on a router/firewall, usually connecting two networks together, and translates the private (not globally unique) addresses in the internal network into legal addresses, before packets are forwarded to another network.
As part of this capability, NAT can be configured to advertise only one address for the entire network to the outside world. This provides additional security by effectively hiding the entire internal network behind that address. NAT offers the dual functions of security and address conservation. We were expecting to bid NAT a farewell with launch of IPv6 but NAT has re-emerged in a new form i.e. 6to4 NAT or NAT-PT (Protocol Translation). I am sure it has bought itself few more golden years.
Hot Standby Router Protocol (HSRP)
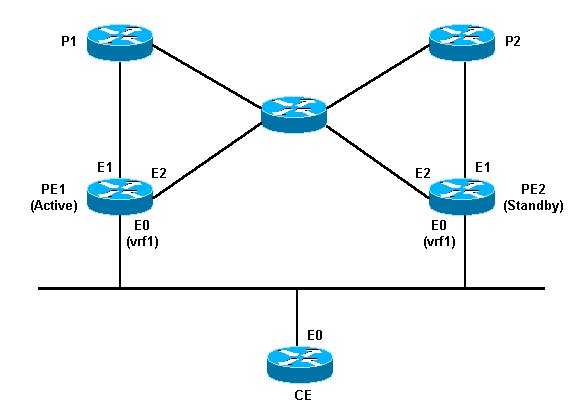

When I was beginner, Redirecting LAN traffic from one router to another without touching a cable was none less than a magic. Even today HSRP would make to my list of best innovations in the field of networking. HSRP provides network redundancy for IP networks, ensuring that user traffic immediately and transparently recovers from first hop failures in network edge devices or access circuits.
By sharing an IP address and a MAC (Layer 2) address, two or more routers can act as a single “virtual” router. The members of the virtual router group continually exchange status messages. This way, one router can assume the routing responsibility of another, should it go out of commission for either planned or unplanned reasons. Hosts continue to forward IP packets to a consistent IP and MAC address, and the changeover of devices doing the routing is transparent. More info about HSRP can be found in RFC2281, You might wish to use our newly launched Request for Comments (RFC) Lookup tool to read this RFC.
Comparable IEEE standard for HSRP is VRRP
IP Service Level Agreement (IP SLA)
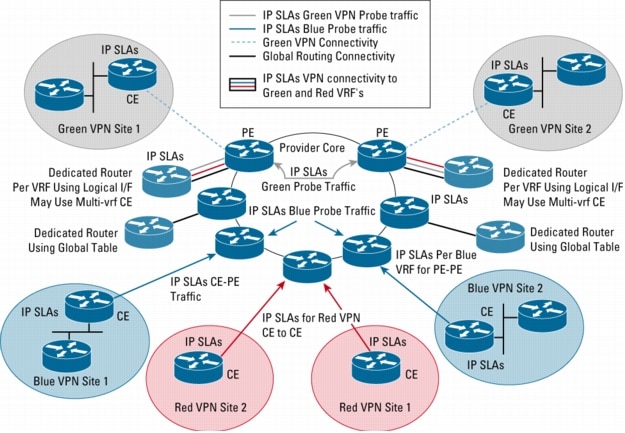

It was never easy to configure failover on internet lines when terminated on Ethernet. Till few year ago, buying a thousand dollars purpose built link load balancer was the only way to do a transparent failover on internet lines on copper. IP SLA allowed us to overcome this challenge in a very simple and easy to configure manner. Cisco IOS IP SLAs collect network performance information in real time: response time, one-way latency, jitter, packet loss, voice quality measurement, and other network statistics. The user can continuously, reliably, and predictably measure network performance and proactively monitor network health. With Cisco IOS IP SLAs, service level monitoring is automated, IP service levels can be assured, network operation can be verified proactively, and network performance can be accurately measured but what interest me most is you can specify a tracking object and a timeout value on your primary internet route, after which you can call an alternate route into your routing table and same can be reverted as soon as you primary link is back online.
Ideally Spanning Tree deserves to be a part of this list but it created more problems than it solved for me. I personally never liked STP much, That’s why STP is not part of my list. So that’s all with my most used.